Ignoble Scorpius
Scenario
Lab Link: Ignoble Scorpius
Your organization has fallen victim to a sophisticated ransomware attack involving BlackSuit Ransomware, attributed to the financially motivated threat actor group Ignoble Scorpius. This attack has encrypted critical files, causing significant operational disruptions. A ransom note has been deployed, demanding payment in cryptocurrency. Although the attackers have not indicated any data theft, they are using the encrypted files to pressure the organization into meeting their demands.
As part of the Incident Response (IR) team, your main priorities are to contain and mitigate the attack, identify the attack vector, and assess the full scope of the compromise. In addition, it is essential to analyze the Tactics, Techniques, and Procedures (TTPs) of Ignoble Scorpius to enhance defenses and prevent future intrusions.
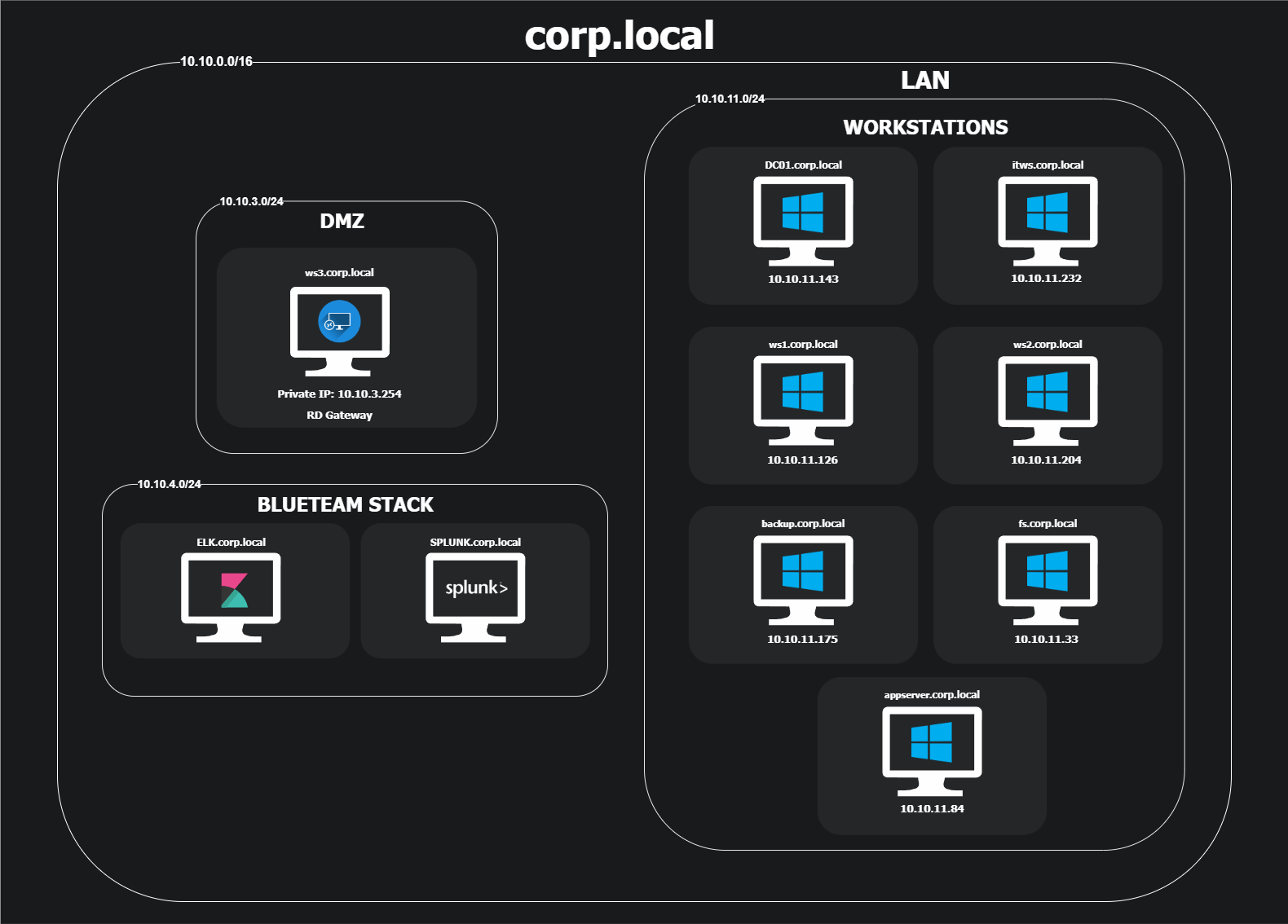
Network Diagram
Below is a network infrastructure diagram, showing key systems and segments.
Reference Labs
Want to dive deeper into the ransomware used by threat actors? Analyze the full sample and uncover its secrets in the BlackSuit Ransomware Lab.
Reconnaissance
| eventcount summarize=false index=*
| dedup index
| fields index|cim_modactions|
|history|
|main|
|summary|| metadata type=sources index=* OR index=_*
| where like(source, "XmlWinEventLog:%")
| table source|XmlWinEventLog:Application|
|XmlWinEventLog:DNS Server|
|XmlWinEventLog:Directory Service|
|XmlWinEventLog:Microsoft-Windows-AppModel-Runtime/Admin|
|XmlWinEventLog:Microsoft-Windows-AppXDeployment/Operational|
|XmlWinEventLog:Microsoft-Windows-AppXDeploymentServer/Operational|
|XmlWinEventLog:Microsoft-Windows-Application-Experience/Program-Telemetry|
|XmlWinEventLog:Microsoft-Windows-Bits-Client/Operational|
|XmlWinEventLog:Microsoft-Windows-CAPI2/Operational|
|XmlWinEventLog:Microsoft-Windows-CodeIntegrity/Operational|
|XmlWinEventLog:Microsoft-Windows-Containers-Wcifs/Operational|
|XmlWinEventLog:Microsoft-Windows-Crypto-NCrypt/Operational|
|XmlWinEventLog:Microsoft-Windows-DNSServer/Audit|
|XmlWinEventLog:Microsoft-Windows-DriverFrameworks-UserMode/Operational|
|XmlWinEventLog:Microsoft-Windows-Forwarding/Operational|
|XmlWinEventLog:Microsoft-Windows-GroupPolicy/Operational|
|XmlWinEventLog:Microsoft-Windows-Kernel-PnP/Configuration|
|XmlWinEventLog:Microsoft-Windows-LAPS/Operational|
|XmlWinEventLog:Microsoft-Windows-LSA/Operational|
|XmlWinEventLog:Microsoft-Windows-NetworkProfile/Operational|get the host:
index=*
| stats count by host|APPSERVER
|BACKUP
|DC01
|FS
|ITWS
|WS1
|WS2
|WS3Initial Access
Q1
Identifying the source IP address of the attacker's machine is crucial for determining the attack's origin and tracking unauthorized access. What IP address was used for initial access to the DMZ machine (RDP Gateway), and what is the SID of the user account used to log in?
Answer Format: **.***.***.***,*-*-*-**-*********-**********-**********-***index=* EventCode=4624 | search LogonType=10 host=WS3 | table _time, EventCode, TargetUserSid, IpAddress | sort -_time|2025-01-29 11:15:34|4624|S-1-5-21-337128598-2364711288-4282874372-500|18.156.176.108|Answer:
18.156.176.108,S-1-5-21-337128598-2364711288-4282874372-500Q2
Determining the initial access timestamp and the attacker's entry method is essential for incident scoping and investigation. At what exact timestamp did the attacker gain initial access to the DMZ machine?
YYYY-MM-DD HH:MMindex=* EventCode=4624 LogonType=10 host=WS3 IpAddress=18.156.176.108
| table _time, EventCode, TargetUserSid, IpAddress
| sort _time
| head 1Answer:
2025-01-29 11:15:34Q3
To accurately classify and analyze the attacker's initial access method on the DMZ machine, consider how the use of compromised credentials could have facilitated unauthorized access. Mapping this activity to a standardized framework for detection engineering and threat hunting is essential. What is the MITRE ATT&CK technique ID associated with this initial access method?
Answer Format: T****The attacker used compromised credentials (the Administrator account) to access an external-facing RDP service (WS3 - RDP Gateway in the DMZ).
This maps to the Initial Access tactic with the technique:
T1078 - Valid Accounts
Answer:
T1078Q4
The attacker initially attempted to access the foothold machine via RDP but lacked sufficient privileges to establish a graphical session. The first compromised account used in these failed RDP attempts was unable to gain interactive access. However, the attacker later switched to another compromised account, which was successfully authenticated and allowed further movement.
What timestamp did the attacker successfully pivot from the DMZ to the internal domain?
YYYY-MM-DD HH:MMindex=* EventCode=4624 host=WS1 IpAddress=10.10.3.254 | table _time, EventCode, TargetUserSid, IpAddress | sort -_timeAnswer:
2025-01-29 11:23Q5
Identifying the compromised account and its SID is key to understanding the attacker's privileges at this stage. Which account did the attacker use during initial access to deploy the beacon on the foothold machine, and what is its SID?
Answer Format: ******,*-*-*-**-**********-********-**********-****get the users by this query
index=* EventCode=4624 host=WS1
| table _time, EventCode, TargetUserName, TargetUserSid, IpAddress, LogonType
| sort _timenow get each user with SID
index=* SubjectUserName=gnunez "S-1-5-21*"
| head 5
| table _time, EventCode, SubjectUserName, SubjectUserSid, hostAnswer:
gnunez,S-1-5-21-3865674213-28386648-2675066931-1127Execution
Q6
During the attack, the adversary deployed an initial payload that served as the main executable within the compromised infrastructure. What is the full path of this first deployed payload?
index=* earliest="01/29/2025:11:23:00" host=WS1 EventCode=1 |search "*gnunez*" (ParentImage="*downloads*" OR ParentImage="*Desktop*" OR ParentImage="*temp*")
| table ParentImage Image ParentCommandLine CommandLine|C:\Users\gnunez\Downloads\Sys.exe|C:\Windows\System32\WindowsPowerShell\v1.0\powershell.exe|"C:\Users\gnunez\Downloads\Sys.exe"|powershell -enc cwBjAGgAdABhAHMAawBzACAALwBjAHIAZQBhAHQAZQAgAC8AdABuACAAIgBVAHAAZABhAHQAZQAiACAALwB0AHIAIAAiAEMAOgBcAFcAaQBuAGQAbwB3AHMAXABTAHkAcwB0AGUAbQAzADIAXABzAHAAbwBvAGwAXABkAHIAaQB2AGUAcgBzAFwAYwBvAGwAbwByAFwAYwByAGUAZAB3AGkAegAuAGUAeABlACIAIAAvAHMAYwAgAGQAYQBpAGwAeQAgAC8AcwB0ACAAMQAyADoAMAAwAA==|
|C:\Users\gnunez\Downloads\Sys.exe|C:\Users\gnunez\AppData\Local\Temp\h.exe|"C:\Users\gnunez\Downloads\Sys.exe"|C:\Users\gnunez\AppData\Local\Temp\h.exe -c All --outputdirectory C:\Users\gnunez\AppData\Local\Temp --zippassword "P@$$w0rd"|
|C:\Users\gnunez\Downloads\Sys.exe|C:\Windows\System32\rundll32.exe|"C:\Users\gnunez\Downloads\Sys.exe"|C:\Windows\system32\rundll32.exe|
|C:\Users\gnunez\Downloads\Sys.exe|C:\Windows\System32\rundll32.exe|"C:\Users\gnunez\Downloads\Sys.exe"|C:\Windows\system32\rundll32.exe|
|C:\Users\gnunez\Downloads\Sys.exe|C:\Windows\System32\cmd.exe|"C:\Users\gnunez\Downloads\Sys.exe"|C:\Windows\system32\cmd.exe /C net group "domain admins" /domain|
|C:\Users\gnunez\Downloads\Sys.exe|C:\Windows\System32\cmd.exe|"C:\Users\gnunez\Downloads\Sys.exe"|C:\Windows\system32\cmd.exe /C nltest /domain_trusts /all_trusts|
|C:\Users\gnunez\Downloads\Sys.exe|C:\Windows\System32\cmd.exe|"C:\Users\gnunez\Downloads\Sys.exe"|C:\Windows\system32\cmd.exe /C nltest /dclist:corp.local|
|C:\Users\gnunez\Downloads\Sys.exe|C:\Windows\System32\cmd.exe|"C:\Users\gnunez\Downloads\Sys.exe"|C:\Windows\system32\cmd.exe /C nslookup -type=SRV _ldap._tcp.dc._msdcs.corp.local|
|C:\Users\gnunez\Downloads\Sys.exe|C:\Windows\System32\cmd.exe|"C:\Users\gnunez\Downloads\Sys.exe"|C:\Windows\system32\cmd.exe /C net view \\ws1|
|C:\Users\gnunez\Downloads\Sys.exe|C:\Windows\System32\rundll32.exe|"C:\Users\gnunez\Downloads\Sys.exe"|C:\Windows\system32\rundll32.exe|
|C:\Users\gnunez\Downloads\Sys.exe|C:\Windows\System32\rundll32.exe|"C:\Users\gnunez\Downloads\Sys.exe"|C:\Windows\system32\rundll32.exe|
|C:\Users\gnunez\Downloads\Sys.exe|C:\Windows\System32\cmd.exe|"C:\Users\gnunez\Downloads\Sys.exe"|C:\Windows\system32\cmd.exe /C whoami /groups|
|C:\Users\gnunez\Downloads\Sys.exe|C:\Windows\System32\cmd.exe|"C:\Users\gnunez\Downloads\Sys.exe"|C:\Windows\system32\cmd.exe /C systeminfo|
|C:\Users\gnunez\Downloads\Sys.exe|C:\Windows\System32\cmd.exe|"C:\Users\gnunez\Downloads\Sys.exe"|C:\Windows\system32\cmd.exe /C whoami /priv|Answer:
C:\Users\gnunez\Downloads\Sys.exeQ7
The payload deployed in Q6 creates a child process that loads DLL modules. What is the process ID of this child process, and which DLL is the first one loaded by it?
Answer Format: ****,*******.***index=* earliest="01/29/2025:11:23:00" host=WS1 EventCode=1
ParentImage="C:\\Users\\gnunez\\Downloads\\Sys.exe" Image="*rundll32.exe"
| table _time, ProcessId, Image, ParentImage, CommandLine
| sort _timewe get the process id
1916index=* earliest="01/29/2025:11:23:00" host=WS1 EventCode=7 ProcessId=1916
| table _time, ProcessId, ImageLoaded
| sort _timeAnswer:
1916,mscoree.dllQ8
Understanding PowerShell patterns for lateral movement aids in identifying the C2 framework module used and enhances detection engineering by mapping the TTPs leveraged by threat actors. Which C2 framework module was used for lateral movement to the File Server (FS), Backup, and App Server?
Answer Format: ******_***index=* earliest="01/29/2025:11:23:00" (host=FS OR host=BACKUP OR host=APPSERVER) EventCode=1
| search "*powershell*"
| table _time, host, CommandLine, Image, ParentImage
| sort _timeAnswer:
psexec_pshPersistence
Q9
Understanding how the attacker maintains persistent access is crucial for identifying long-term threats and preventing further compromise. What is the MITRE ATT&CK technique ID associated with this persistence method, and what is the full file path of the executable used to establish persistence on the WS1 machine?
index=* earliest="01/29/2025:11:21:00" host=WS1 EventCode=1
| search "*gnunez*" (ParentImage="*downloads*" OR ParentImage="*Desktop*" OR ParentImage="*temp*")
| table ParentImage Image ParentCommandLine CommandLinepowershell -enc cwBjAGgAdABhAHMAawBzACAALwBjAHIAZQBhAHQAZQAgAC8AdABuACAAIgBVAHAAZABhAHQAZQAiACAALwB0AHIAIAAiAEMAOgBcAFcAaQBuAGQAbwB3AHMAXABTAHkAcwB0AGUAbQAzADIAXABzAHAAbwBvAGwAXABkAHIAaQB2AGUAcgBzAFwAYwBvAGwAbwByAFwAYwByAGUAZAB3AGkAegAuAGUAeABlACIAIAAvAHMAYwAgAGQAYQBpAGwAeQAgAC8AcwB0ACAAMQAyADoAMAAwAA==decode
schtasks /create /tn "Update" /tr "C:\Windows\System32\spool\drivers\color\credwiz.exe" /sc daily /st 12:00Answer:
T1053,C:\Windows\System32\spool\drivers\color\credwiz.exeQ10
The attacker is utilizing various techniques to maintain access to domain machines. What is the MITRE ATT&CK sub-technique ID used to achieve persistence, and what is the full file path of the executable deployed for persistence on the Domain Controller?
Answer Format: T****.***,C:\*******\********\***\*************.***Event ID 7045 indicates that a new Windows service was installed on the system
index=* earliest="01/29/2025:11:23:00" host=DC01 EventCode=7045
| table _time, ServiceName, ImagePath, ServiceFileName
| sort _time|2025-01-29 13:45:27|99f6661|\\DC01.corp.local\ADMIN$\99f6661.exe||
|2025-01-29 14:53:08|Core Messaging Service|C:\Windows\System32\ras\Coremessaging.exe||Service 1: 99f6661
- Time: 2025-01-29 13:45:27
- Path:
\\DC01.corp.local\ADMIN$\99f6661.exe - Random name, executing from network share (likely initial execution, not persistence)
Service 2: Core Messaging Service
- Time: 2025-01-29 14:53:08
- Path:
C:\Windows\System32\ras\Coremessaging.exe - This is your persistence mechanism!
Why Service 2 is Malicious:
- Masquerading: Mimics legitimate "CoreMessaging" Windows service
- Wrong Location: Should NOT be in
C:\Windows\System32\ras\(Remote Access Service directory) - Persistence: Survives reboots via Windows Service
MITRE ATT&CK: T1543.003 - Create or Modify System Process: Windows Service
This technique allows the attacker to maintain persistent access to the Domain Controller by installing their beacon as a Windows service that automatically starts with the system.
Answer:
T1543.003,C:\Windows\System32\ras\Coremessaging.exeCredential Access & Privilege Escalation
Q11
The attacker appears to have attempted multiple credential access methods targeting the Active Directory environment before executing lateral movement to the domain controller. What is the MITRE ATT&CK technique ID of the first credential access method used, and what is the account name involved?
Answer Format: T****.***,***-*********hint 1 Event ID 4768 with PreAuthType=0
EventCode 4768 = Kerberos Authentication Ticket (TGT) Request PreAuthType=0 = No pre-authentication (vulnerable to AS-REP Roasting) This is T1558.004 - AS-REP Roasting, where attackers request Kerberos tickets for accounts that don't require pre-authentication, allowing them to crack passwords offline.
now lets get the target username from the hint 1 no need for the two other hints
index=* earliest="01/29/2025:11:23:00" EventCode=4768 PreAuthType=0
| table _time, TargetUserName, Target_User_Name, user
| sort _time|2025-01-29 12:14:15|svc-legacyapp|svc-legacyapp|svc-legacyapp|Answer:
T1558.004,svc-legacyappQ12
The attacker utilized a service account for lateral movement from WS1. Before executing the movement, the attacker requested the account's credentials or tickets. At what timestamp did this request take place?
YYYY-MM-DD HH:MMwe will use EventCode=4769 for Kerberos service ticket request failed
index=* earliest="01/29/2025:12:00:00" latest="01/29/2025:14:00:00" EventCode=4648 host=WS1
| search TargetServerName="DC01*" OR TargetServerName="*dc01*"
| table _time, SubjectUserName, TargetUserName, TargetServerName, IpAddress
| sort _time2025-01-29 13:45:06 gnunez svc-fileshare DC01.corp.local 10.10.11.143
2025-01-29 13:45:27 gnunez svc-fileshare DC01.corp.local 10.10.11.143index=* earliest="01/29/2025:12:00:00" latest="01/29/2025:14:00:00" EventCode=4769
| search "svc-fileshare"
| table _time, Account_Name, Service_Name, ServiceName, Ticket_Encryption_Type, TicketEncryptionType
| sort _time|2025-01-29 12:18:57|||svc-fileshare||0x17|
|2025-01-29 13:45:06|||krbtgt||0x12|
|2025-01-29 13:45:06|||DC01$||0x12|- 12:14 - AS-REP Roasting of svc-legacyapp
- 12:18 - Kerberoasting of svc-fileshare (TGS request with RC4 encryption)
- 13:45 - Used cracked svc-fileshare credentials to access DC01
Answer:
2025-01-29 12:18Q13
Identifying the account used for lateral movement is essential for understanding the attacker's privilege escalation strategy and tracking their movement within the network. What account did the attacker use to perform lateral movement from WS1?
Answer Format: ***-*********Event ID 4769 logs a failed Kerberos Service Ticket Granting Service (TGS) request on a domain controller, indicating an issue with an account trying to access a service
no need for any query we have it before:
index=* earliest="01/29/2025:12:00:00" latest="01/29/2025:14:00:00" EventCode=4648 host=WS1
| search TargetServerName="DC01*" OR TargetServerName="*dc01*"
| table _time, SubjectUserName, TargetUserName, TargetServerName, IpAddress
| sort _time2025-01-29 13:45:06 gnunez svc-fileshare DC01.corp.local 10.10.11.143
2025-01-29 13:45:27 gnunez svc-fileshare DC01.corp.local 10.10.11.143Answer:
svc-fileshareQ14
What is the MITRE ATT&CK sub-technique ID for the previous credential access method, and what is the full file path used to store the output of the credential access?
Answer Format: T****.***,C:\*****\******\*.***The MITRE ATT&CK technique is T1558.003 (Kerberoasting), and we're looking for the output file path where the TGS ticket was saved.
EventCode=11 = File created This will show files created by the attacker around the Kerberoasting timestamp (12:18:57).
index=* earliest="01/29/2025:12:15:00" latest="01/29/2025:12:25:00" host=WS1 EventCode=11
| search TargetFilename="*.txt"
| table _time, Image, TargetFilename
| sort _timeAnswer:
T1558.003,C:\Users\Public\2.txtQ15
The attacker sought to gain higher privileges after landing on the domain controller. What is the Process ID (PID) used for Credential Access on the domain controller, and what was the granted access associated with it?
Answer Format: **** ,0x****index=* earliest="01/29/2025:13:45:00" host=DC01 EventCode=10
| search TargetImage="*lsass.exe"
| table _time, SourceImage, TargetImage, SourceProcessId, GrantedAccess, CallTrace
| sort _time|2025-01-29 14:00:34|C:\Windows\system32\rundll32.exe|C:\Windows\system32\lsass.exe|6508|0x1010|C:\Windows\SYSTEM32\ntdll.dll+a6564\|C:\Windows\System32\KERNELBASE.dll+2c48d\|UNKNOWN(000001FBCDD38120)|Answer:
6508,0x1010Q16
The previous credential access attempt allowed the attacker to obtain the credentials of an account later used for ransomware execution. What is the fully qualified domain name (FQDN) of the user account associated with this execution?
Answer Format: ****\*****- 15:30:23 - DC01:
CORP\fwardusing mstsc.exe (RDP) - 15:33:38 - APPSERVER:
CORP\fwardactivity - 15:37:44 - FS:
CORP\fwardactivity - 15:38:57 - BACKUP:
CORP\fwardactivity
index=* earliest="01/29/2025:14:00:34" EventCode=1
| table _time, host, User, Account_Name, Image, CommandLine
| sort _timeAnswer:
CORP\fwardDefense Evasion
Q17
What is the Process ID (PID) into which the attacker injected their beacon on the Domain Controller to evade detection?
Answer: ****index=* earliest="01/29/2025:11:21:00" host=WS1 EventCode=1
| search "*gnunez*" (ParentImage="*downloads*" OR ParentImage="*Desktop*" OR ParentImage="*temp*")
| table ParentImage Image ParentCommandLine CommandLinethen get this:
index=* earliest="01/29/2025:13:45:00" host=DC01 EventCode=8
| table _time, SourceImage, TargetImage, TargetProcessId, StartAddress, StartFunction
| sort _time|2025-01-29 13:49:13|C:\Windows\System32\rundll32.exe|C:\Windows\System32\svchost.exe|2448|0x0000025B2CED0000|EventCode=8 - CreateRemoteThread detected process injection on DC01:
- Time: 2025-01-29 13:49:13
- Source:
C:\Windows\System32\rundll32.exe(malicious beacon) - Target:
C:\Windows\System32\svchost.exe(legitimate Windows process) - TargetProcessId: 2448
Answer:
2448Q18
During the investigation, you identified the process that was injected to enable the transfer of the ransomware executable to the App Server. What is the Process ID (PID) of this target process, and what is the remote Thread ID associated with it at the time of injection?
Answer Format: ****,****EventCode=8 = CreateRemoteThread on APPSERVER
- TargetProcessId = The PID of the injected process
- NewThreadId = The remote thread ID created during injection
index=* earliest="01/29/2025:15:00:00" host=APPSERVER EventCode=8
| table _time, SourceImage, TargetImage, TargetProcessId, NewThreadId, StartAddress
| sort _timeAnswer:
1696,3960Q19
During lateral movement to the Domain Controller, the attacker modified the named pipe name, deviating from the C2 framework's default convention for this technique. What is the name of the pipe used in this movement?
Answer Format: \pipe\****.*****.*****.*******************EventCode=17 = Pipe Created EventCode=18 = Pipe Connected
index=* earliest="01/29/2025:13:45:00" latest="01/29/2025:14:00:00" host=DC01 (EventCode=17 OR EventCode=18)
| table _time, EventCode, PipeName, Image
| sort _time2025-01-29 13:45:28 17 \MSSE-9411-server \\DC01.corp.local\ADMIN$\99f6661.exe
2025-01-29 13:45:29 17 \pipe\mojo.12780.15432.8094946700812862752 C:\Windows\System32\rundll32.exe
2025-01-29 13:45:29 18 \MSSE-9411-server \\DC01.corp.local\ADMIN$\99f6661.exeAnswer:
\pipe\mojo.12780.15432.8094946700812862752Q20
The attacker appears to have used the same technique but with different methods, renaming the pipe to resemble common Windows system pipe names to evade detection. What is the pipeline name used for lateral movement to the Backup Server?
Answer Format: \pipe\******.******************.*****.****************.********index=* earliest="01/29/2025:15:30:00" latest="01/29/2025:16:30:00" host=BACKUP (EventCode=17 OR EventCode=18)
| table _time, EventCode, PipeName, Image
| sort _timeAnswer:
\pipe\PSHost.133817624228059307.21636.DefaultAppDomain.powershellQ21
When the attacker faced a blocking error while attempting lateral movement to the App Server, they executed a command to bypass the defense mechanism. What command did the attacker use to overcome this restriction?
Answer Format: "C:\Windows\system32\*****.exe" *********** *** *********** ***** ***index=* earliest="01/29/2025:15:30:00" host=APPSERVER EventCode=1
| search "*firewall*"
| table _time, Image, CommandLine
| sort _time2025-01-29 16:31:31 C:\Windows\System32\netsh.exe "C:\Windows\system32\netsh.exe" advfirewall set allprofiles state offAnswer:
"C:\Windows\system32\netsh.exe" advfirewall set allprofiles state offDiscovery
Q22
After gaining access to the WS1 machine within the domain, what was the first command executed by the attacker to enumerate account privileges and group memberships?
Answer Format: ****** /****index=* earliest="01/29/2025:11:23:00" host=WS1 EventCode=1
| search ParentImage="*Sys.exe" (CommandLine="*whoami*")
| table _time, CommandLine
| sort _time2025-01-29 11:34:15 C:\Windows\system32\cmd.exe /C whoami /priv
2025-01-29 11:35:54 C:\Windows\system32\cmd.exe /C whoami /groups
2025-01-29 11:55:05 C:\Windows\system32\cmd.exe /C net view \\ws1
2025-01-29 12:06:16 C:\Windows\system32\cmd.exe /C nltest /dclist:corp.local
2025-01-29 12:07:13 C:\Windows\system32\cmd.exe /C nltest /domain_trusts /all_trusts
2025-01-29 12:09:51 C:\Windows\system32\cmd.exe /C net group "domain admins" /domainAnswer:
whoami /privQ23
Detecting C2 framework activity involves identifying unique indicators such as named pipes. What pipe name was used for network scanning and reconnaissance?
Answer Format: \******_****index=* earliest="01/29/2025:11:30:00" latest="01/29/2025:12:15:00" host=WS1 (EventCode=17 OR EventCode=18)
| table _time, EventCode, PipeName, Image
| sort _timeAnswer:
\postex_8e88Q24
After completing network mapping on the WS1 machine, the attacker proceeded with domain enumeration to gather information about the domain structure. What was the first command executed to passively identify all Domain Controllers (DCs) within the domain?
Answer Format: ******** -****=*** _****._***.**._*****.****.*****index=* earliest="01/29/2025:11:30:00" latest="01/29/2025:12:10:00" host=WS1 EventCode=1
| search CommandLine="*nslookup*"
| table _time, CommandLine
| sort _timeAnswer:
nslookup -type=SRV _ldap._tcp.dc._msdcs.corp.localQ25
Tracing the execution source of a script used for host discovery is crucial for mapping attacker movements and understanding the full attack chain. What is the full file path of the file that executed the PowerShell script on the compromised machines?
Answer Format: *:\********\****.***index=* earliest="01/29/2025:14:00:00" EventCode=1
| search CommandLine="*.bat*"
| table _time, host, Image, CommandLine
| sort _timecmd.exe /k "C:\PerfLogs\Exec.bat"Answer:
C:\PerfLogs\Exec.batQ26
What is the full file path of the output folder where the PowerShell script used for host discovery saved its output?
Answer Format: *:\*******\********\******C:\Windows\System32\resultQ27
What is the full path of the command executed by the attacker to retrieve active user session information, and what is the Parent Process ID (PID) of the process executing this action on the domain controller?
Answer Format: C:\*******\********\***.*** /* *******,****host="DC01" EventID=1 earliest="01/29/2025:13:45:00"
| table UtcTime, parent_process_name, process_name, ParentImage, Image, CommandLine, ParentProcessId, ProcessId
| rename parent_process_name as "Parent Process Name", process_name as "Child Process Name", ParentImage as "Parent Process Path",C:\Windows\system32\cmd.exe /C qwinsta,2448Q28
The attacker utilized a well-known enumeration tool to collect detailed information about domain relationships. What is the full path of the output file stored on the WS1 machine, and what password was used to secure the zipped file?
Answer Format: *:\*****\******\*******\*****\****,*@$$****Answer:
c:\users\gnunez\appdata\local\temp,P@$$w0rdQ29
What was the full command line executed by the attacker on the File Server to identify all Domain Controllers (DCs) in the environment, analyze the replication structure, and locate offsite DCs or backups to maximize the spread of encryption across the network?
Answer: *:\*****\*****\*******\*****\****\**.exe -* "**=****,**=*****" -********index=* earliest="01/29/2025:15:30:00" host=FS EventCode=1
| search CommandLine="*.exe*" (CommandLine="*DC=*" OR CommandLine="*ldap*" OR CommandLine="*domain*")
| table _time, Image, CommandLine
| sort _timeAnswer:
C:\Users\fward\AppData\Local\Temp\af.exe -b "DC=corp,DC=local" -showreplQ30
Analyzing the attacker's file access activity helps uncover their intentions, especially when targeting financial enterprise data. What was the first file the attacker accessed or opened on the File Server (FS)?
Answer Format: *********_*********_******_**_****.***host="fs" EventID=1 ("*.pdf")
| sort _time
| head 1
| table _time, ParentCommandLine, CommandLine|"C:\Program Files\Mozilla Firefox\firefox.exe" -osint -url C:\Shares\Finance\quarterly_financial_report_q3_2024.pdf|
"C:\Program Files\Mozilla Firefox\firefox.exe" -contentproc --channel=2332 -parentBuildID 20241110231641 -prefsHandle 2324 -prefMapHandle 2320 -prefsLen 23784 -prefMapSize 261230 -win32kLockedDown -appDir "C:\Program Files\Mozilla Firefox\browser" - {8ec63910-a350-4ade-b099-ee6b9fadf217} 5456 "\\.\pipe\gecko-crash-server-pipe.5456" 2 socketAnswer:
quarterly_financial_report_q3_2024.pdfLateral Movement
Q31
Tracking the timestamp of lateral movement to the Domain Controller is crucial for understanding the attack timeline, detecting unauthorized access, and correlating events for incident response. At what timestamp did the attacker successfully move laterally to the Domain Controller?
YYYY-MM-DD HH:MMWe already found this earlier! From the EventCode 4648 query showing credential usage:
2025-01-29 13:45:06 gnunez svc-fileshare DC01.corp.local 10.10.11.143Answer:
2025-01-29 13:45Q32
The attacker deployed the first beacon on the Domain Controller. What was the parent command-line path used to execute this beacon?
Answer Format: \\****.****.*****\*****$\*******.***Looking at the earlier results from the parent/child process table, I can see:
2025-01-29 13:45:29.185 99f6661.exe rundll32.exe \\DC01.corp.local\ADMIN$\99f6661.exeAnswer:
\\DC01.corp.local\ADMIN$\99f6661.exeQ33
Identifying the first recorded RDP session initiated from the Domain Controller helps in tracking attacker movement, detecting potential privilege abuse, and correlating events for incident response and containment. When did the first recorded event in the attacker's series of RDP sessions to multiple machines within the domain occur?
YYYY-MM-DD HH:MMLooking at the earlier process creation data from DC01, I saw:
2025-01-29 15:30:23 DC01 CORP\fward mstsc.exe "C:\Windows\system32\mstsc.exe"Answer:
2025-01-29 15:30Q34
Determining the timestamp of lateral movement to the File Server (FS) is crucial for focusing the investigation, correlating activities on the compromised machine, and identifying subsequent attacker actions. When did the attacker execute lateral movement to the File Server (FS) using the beacon?
YYYY-MM-DD HH:MMLooking at the earlier results from the psexec_psh lateral movement query, I found:
2025-01-29 15:41:11 FS powershell -nop -w hidden -encodedcommand ...
2025-01-29 15:41:11 FS C:\Windows\system32\cmd.exe /b /c start /b /min powershell ...index=* earliest="01/29/2025:15:00:00" host=FS
| search CommandLine="*cmd.exe /b /c start /b /min powershell*"
| table _time, ParentImage, CommandLine
| sort _time
| head 1Answer:
2025-01-29 15:41Q35
Identifying the timestamp of lateral movement to the Backup Server is essential for mapping the attacker's progression, detecting potential data exfiltration or ransomware deployment, and strengthening defense strategies. When did the attacker execute lateral movement to the Backup Server using the beacon?
YYYY-MM-DD HH:MMindex=* earliest="01/29/2025:15:00:00" host=BACKUP EventCode=1
| search (CommandLine="*powershell*" AND CommandLine="*-encodedcommand*") OR ParentImage="*services.exe"
| table _time, ParentImage, Image, CommandLine
| sort _timeAnswer:
2025-01-29 16:18Q36
Identifying the timestamp of lateral movement to the App Server is crucial for correlating attack phases and detecting unauthorized access patterns. When did the attacker move laterally to the App Server using the beacon?
YYYY-MM-DD HH:MMAnswer:
2025-01-29 16:32Command and Control
Q37
Identifying the Command-and-Control (C2) server's IP address is crucial for tracking attacker infrastructure, blocking malicious communication, and preventing further compromise. What is the IP address of the C2 server used to communicate with the deployed payloads?
Answer Format: **.***.***.**index=* host="ws1" EventCode=3
| search "*sys.exe*"
| table _time, DestinationIp
| sort _timeAnswer:
18.197.126.91Q38
Threat intelligence platforms play a key role in detecting and attributing malicious infrastructure, aiding in proactive defense and threat hunting. Based on the ThreatFox IOC database, which platform provided information on this C2 server's IP address?
censysRansomware Distribution & Execution
Q39
Identifying the ransom note file name is crucial for determining the scope of the attack, recognizing the ransomware variant, and pinpointing affected machines. What is the exact name of the ransom note left by the attacker?
Answer Format: ******.*********.***index=* earliest="01/29/2025:14:00:00" EventCode=11
| search TargetFilename="*.txt" OR TargetFilename="*readme*" OR TargetFilename="*ransom*" OR TargetFilename="*blacksuit*"
| table _time, host, TargetFilename, Image
| sort _timeAnswer:
readme.blacksuit.txtQ40
While investigating the infected machines, you discovered the ransomware encryption process running on the system. What is the full file path of the ransomware executable?
Answer Format: *:\*****\*****.***index=* earliest="01/29/2025:16:00:00" EventCode=11
| search TargetFilename="C:\\Temp\\*.exe" OR TargetFilename="C:\\Users\\*.exe" OR TargetFilename="*blacksuit*"
| table _time, host, TargetFilename
| sort _timeAnswer:
C:\Users\bfsvc.exeQ41
Determining the timestamp of ransomware execution is essential for identifying the attack's entry point and understanding the initial infection timeline. When did the ransomware execution occur on the first infected machine?
YYYY-MM-DD HH:MM2025-01-29 16:41:50 APPSERVER C:\Users\bfsvc.exe (FIRST)
2025-01-29 16:41:53 BACKUP C:\Users\bfsvc.exe
2025-01-29 16:41:55 FS C:\Users\bfsvc.exeAnswer:
2025-01-29 16:44Q42
The attacker appears to have used a text file to copy and paste the correct command for executing the ransomware. What is the name of this file?
Answer Format: *****.***index=* earliest="01/29/2025:16:00:00" EventCode=1 Image="*notepad.exe"
| table _time, host, CommandLine
| sort _timeAnswer:
N1F10.txtQ43
Ransomware groups often use trackers, such as unique IDs in ransom notes, to generate a specific URL for victims to access the payment site. What was the full command executed by the attacker to launch the ransomware, including the assigned ID?
Answer Format: *****.*** -** ********************************index=* earliest="01/29/2025:16:00:00" EventCode=1
| search Image="*bfsvc.exe" OR ParentCommandLine="*bfsvc*"
| table _time, host, ParentImage, ParentCommandLine, Image, CommandLine
| sort _timeAnswer:
bfsvc.exe -id YimIgWT0orzu9T6rEgDncsPdAZFfXRNCAll Content
Doom
The organization suddenly discovered that critical files across system devices were encrypted, with ransom notes found on affected machines, indicating a ransomware attack. The encryption impacted the Domain Controller, file servers, and multiple workstations simultaneously across the entire domain.
Double Dragon
On August 25, 2025, CoreTech's SOC spotted unusual activity on a workstation, hinting at a breach. Suspicious processes and network activity spread to critical servers, threatening data and systems.
GoldenSpray
As a cybersecurity analyst at SecureTech Industries, you've been alerted to unusual login attempts and unauthorized access within the company's network. Initial indicators suggest a potential brute-force attack on user accounts.
Latrodectus LunarSpider
On October 16, 2025, CorpLocal's security team spotted a single workstation acting up, followed by a ransom note and proof of massive data theft.
Nitrogen
On September 10, 2025, trustwave.lab's SOC team identified suspicious activity originating from a user workstation.
RansomHub
On October 19, 2025, the SOC team detected anomalous RDP authentication patterns on a public-facing workstation, including hundreds of failed login attempts followed by successful authentications from an unknown external IP address.
Revil
You are a Threat Hunter working for a cybersecurity consulting firm. One of your clients has been recently affected by a ransomware attack that caused the encryption of multiple of their employees' machines.
ShadowRoast
As a cybersecurity analyst at TechSecure Corp, you have been alerted to unusual activities within the company's Active Directory environment.
